Technical Blog
-

In-depth Analysis and Application Comparison of TAP and SPAN Network Traffic Data Acquisition Methods
In the fields of network operation and maintenance, troubleshooting, and security analysis, accurately and efficiently acquiring network data streams is the foundation for conducting various tasks. As two mainstream network data acquisition technologies, TAP (Test Access...Read more -

Mylinking™ Network Packet Brokers to Capture, Preprocess and Forward Network Traffic OSI Model Layers to your right tools
Mylinking™ Network Packet Brokers supported Network Traffic Dynamic Load Balancing: The load balance Hash algorithm and session-based weight sharing algorithm according to L2-L7 layer characteristics to ensure that the port output traffic dynamic of load balancing. And M...Read more -

As a skilled Network Engineer, do you understand the 8 common Network Attacks?
Network engineers, on the surface, are just "technical laborers" who build, optimize, and troubleshoot networks, but in reality, we are the "first line of defense" in cybersecurity. A 2024 CrowdStrike report showed that global cyberattacks increased by 30%, with Chinese ...Read more -

What is the Intrusion Detection System(IDS) and Intrusion Prevention System(IPS)?
Intrusion Detection System (IDS) is like the scout in the network, the core function is to find the intrusion behavior and send an alarm. By monitoring network traffic or host behavior in real time, it compares the preset "attack signature library" (such as known virus c...Read more -
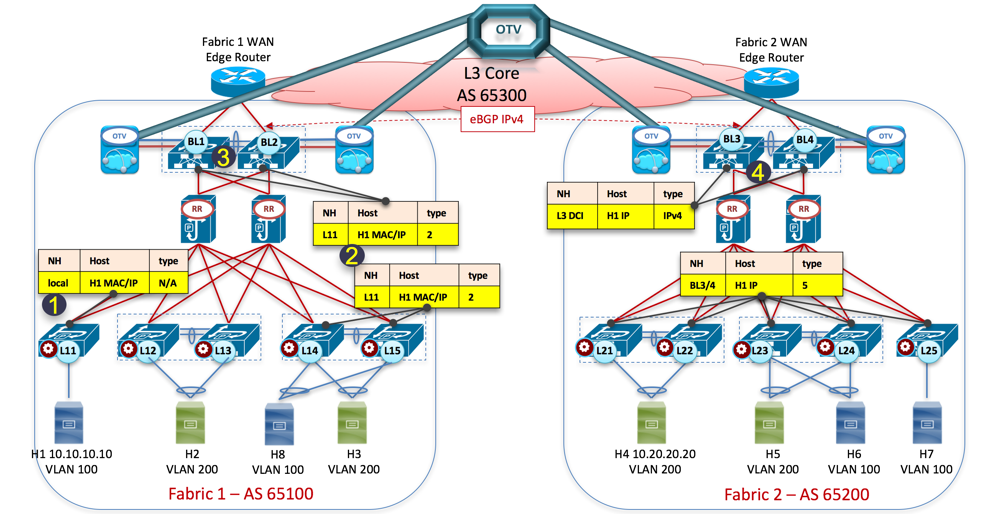
VxLAN(Virtual eXtensible Local Area Network) Gateway: Centralized VxLAN Gateway or Distributed VxLAN Gateway?
To discuss VXLAN gateways, we must first discuss VXLAN itself. Recall that traditional VLANs (Virtual Local Area Networks) use 12-bit VLAN IDs to divide networks, supporting up to 4096 logical networks. This works fine for small networks, but in modern data centers, with...Read more -
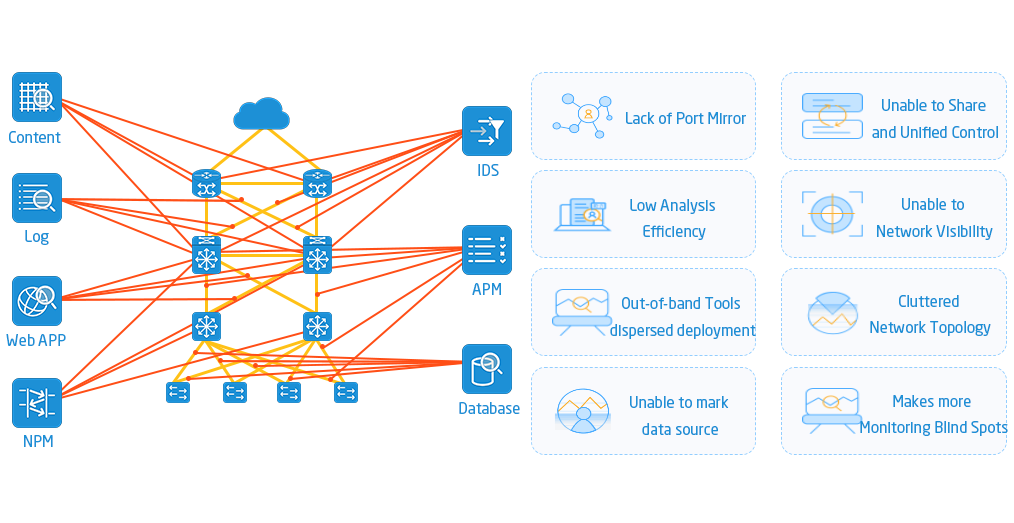
Network Monitoring “Invisible Butler” – NPB: Nework Traffic Management Legend Artifact in the Digital Age
Driven by digital transformation, enterprise networks are no longer simply "a few cables connecting computers." With the proliferation of IoT devices, the migration of services to the cloud, and the increasing adoption of remote work, network traffic has exploded, like t...Read more -

Network Tap vs SPAN Port Mirror, which Network Traffic Capturing is better for your Network Monitoring and Security?
TAPs (Test Access Points), also known as also known as Replication Tap, Aggregation Tap, Active Tap, Copper Tap, Ethernet Tap, Optical Tap, Physical Tap, etc. Taps are a popular method for acquiring network data. They provide comprehensive visibility into network data fl...Read more -

Network Traffic Analysis and Network Traffic Capturing are the Key Technologies to Ensure your Network Performance and Security
In today's digital age, Network Traffic Analysis and Network Traffic Capturing/Collection have become the key technologies to ensure Network Performance and Security. This article will dive into these two areas to help you understand their importance and use cases, and i...Read more -

Decryption IP Fragmentation and Reassembly: Mylinking™ Network Packet Broker Identifies IP Fragmented Packets
Introduction We all know the principle of classification and non-classification principle of IP and its application in network communication. IP fragmentation and reassembling is a key mechanism in the process of packet transmission. When the size of a packet exceeds the...Read more -

From HTTP to HTTPS: Understanding TLS, SSL and Encrypted Communication in Mylinking™ Network Packet Brokers
Security is no longer an option, but a required course for every Internet technology practitioner. HTTP, HTTPS, SSL, TLS - Do you really understand what's going on behind the scenes? In this article, we will explain the core logic of modern encrypted communication protoc...Read more -

Mylinking™ Network Packet Broker(NPB): Illuminating the Dark Corners of Your Network
In today's complex, high-speed, and often encrypted network environments, achieving comprehensive visibility is paramount for security, performance monitoring, and compliance. Network Packet Brokers (NPBs) have evolved from simple TAP aggregators into sophisticated, inte...Read more -

What can Mylinking™ Network Packet Broker do for Network Virtual Technology? VLAN vs VxLAN
In modern network architecture, VLAN (Virtual Local Area Network) and VXLAN (Virtual Extended Local Area Network) are the two most common network virtualization technologies. They may seem similar, but there are actually a number of key differences. VLAN (Virtual Local...Read more
-

Tel
-

E-mail
-

Skype
-

Top












