Have you ever heard of a network tap? If you work in the field of networking or cybersecurity, you may be familiar with this device. But for those who aren’t, it can be a mystery.
In today’s world, network security is more important than ever before. Companies and organizations rely on their networks to store sensitive data and communicate with clients and partners. How can they ensure their network is secure and free from unauthorized access?
This article will explore what a network tap is, how it works, and why it is an essential tool for network security. So let’s dive in and learn more about this powerful device.
What is a Network TAP (Terminal Access Point)?
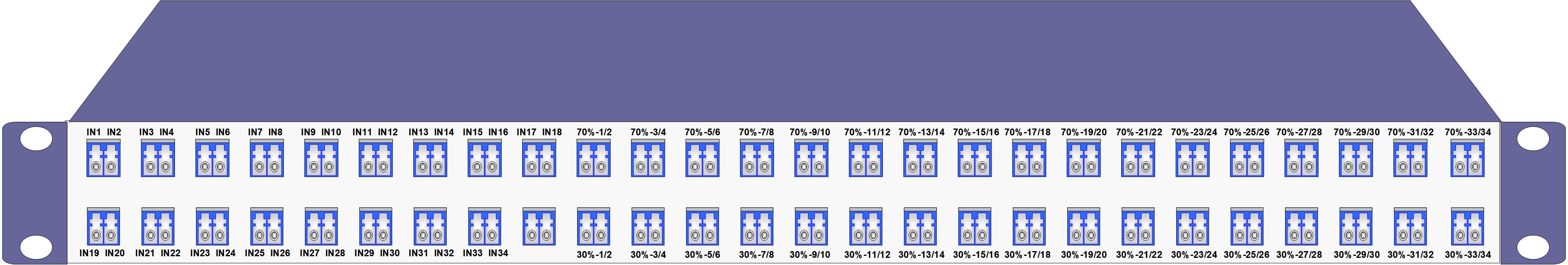
Network TAPs are essential for successful and secure network performance. They provide the means to monitor, analyze, track, and secure network infrastructures. Network TAPs create a “copy” of the traffic, enabling various monitoring devices access to that information without interfering with the original flow of data packets.
These devices are strategically positioned throughout the network infrastructure to ensure the most effective monitoring possible.
Organizations can install network TAPs at points they feel should be observed, including but not limited to locations for gathering data, analysis, general monitoring, or more critical such as intrusion detection.
The network TAP device does not alter the existing state of any packet on the active network; it simply creates a replica of each packet sent so that it can be relayed through its interface connected to monitoring devices or programs.
The copying process is executed without stressing performance capacity since it does not interfere with normal operations in the wire after tapping is complete. Therefore, enabling organizations an extra layer of security while detecting and alerting suspicious activity on their network and keeping an eye out for latency problems that can occur during peak usage times.
How Does a Network TAP Work?
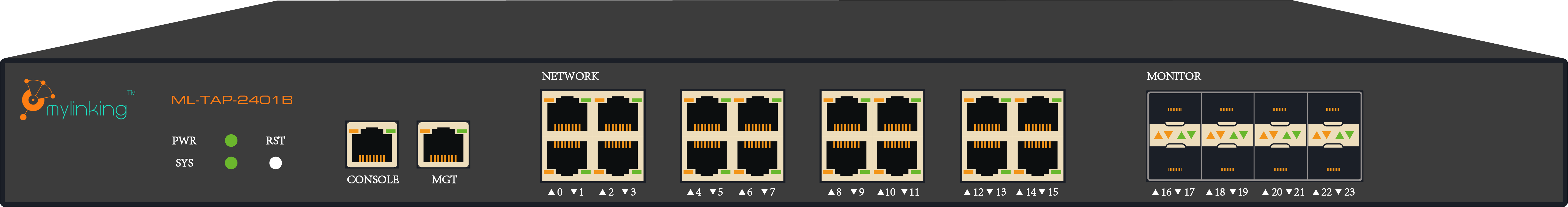
Network TAPs are sophisticated equipment that enables administrators to assess the performance of their entire network without disrupting its functioning. They are external devices used to monitor user activity, detect malicious traffic and protect the network security by allowing for deeper analysis of the data flowing in and out of it. Network TAPs bridge the physical layer at which packets travel across cables and switches and the upper layers where applications reside.
A Network TAP acts as a passive port switch that opens up two virtual ports to capture all incoming and outgoing traffic from any network connections passing through it. The device is designed to be 100% non-intrusive, so while it enables comprehensive monitoring, sniffing, and filtering of data packets, Network TAPs do not disrupt or interfere with the performance of your network in any way.
Furthermore, they act only as channels for channeling relevant data to designated monitoring points; this means that they cannot analyze or evaluate the information they gather – requiring another third-party tool to be able to do so. This allows administrators precise control and flexibility when it comes to tailoring how they can best utilize their Network TAPs while continuing operations uninterruptedly on the rest of their network.
Why Do We Need a Network TAP?
Network TAPs provide the foundation for having a comprehensive and robust visibility and monitoring system on any network. By tapping into the communication medium, they can identify data on the wire so it can be streamed to other security or monitoring systems. This vital component of network visibility ensures that all of the data present on the line is not missed as traffic passes through, meaning no packets are ever dropped.
Without TAPs, a network cannot be fully monitored and managed. IT administrators can reliably monitor for threats or gain granular insight into their networks that out-of-band configurations would otherwise hide by providing access to all traffic information.
As such, an exact copy of incoming and outgoing communications is provided, allowing organizations to investigate and act quickly on any suspicious activity they may encounter. For organizations’ networks to be secure and reliable in this modern age of cybercrime, using a network TAP should be considered mandatory.
Types of Network TAPs and How They Work?
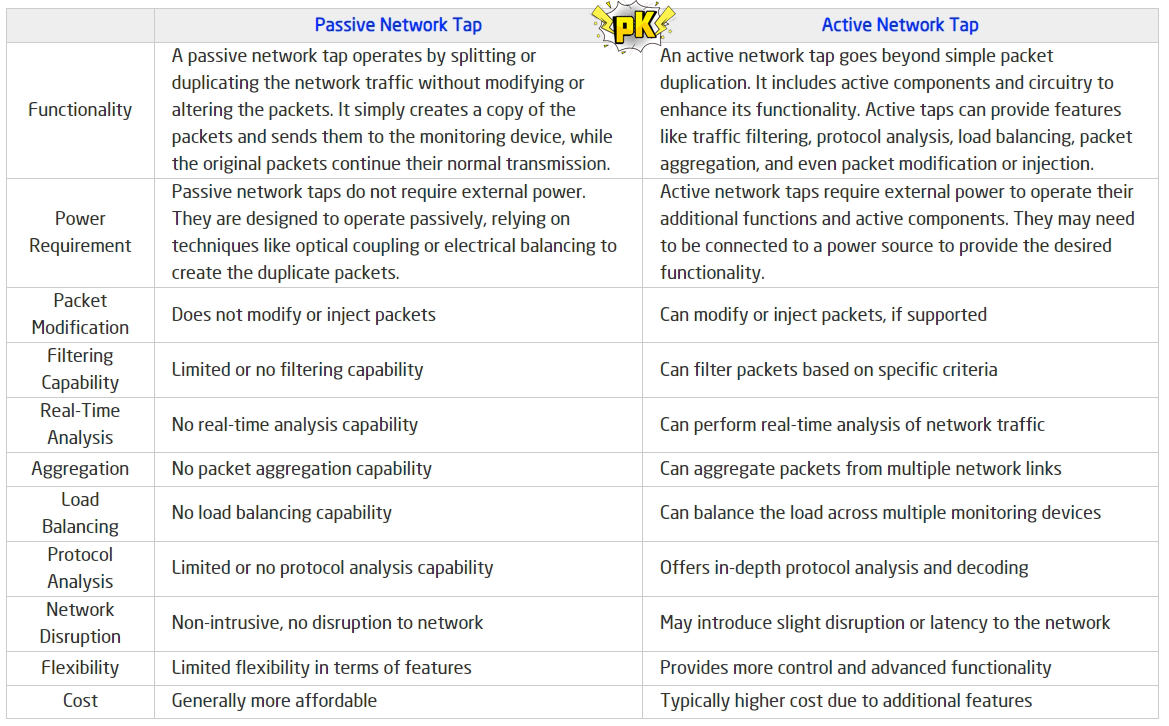
When it comes to accessing and monitoring network traffic, there are two primary types of TAPs – Passive TAPs and Active TAPs. Both provide a convenient and secure way to access a data stream from a network without disrupting the performance or adding additional latency to the system.
A passive TAP operates by examining the electrical signals that pass through a normal point-to-point cable link between two devices, such as between computers and servers. It provides a connection point allowing an external source, such as a router or sniffer, to access the signal flow while still passing through its original destination unaltered. This type of TAP is used when monitoring time-sensitive transactions or information between two points.
An active TAP functions much like its passive counterpart but has an added step in the process – introducing a signal regeneration feature. By leveraging signal regeneration, an active TAP ensures information can be accurately monitored before it proceeds further down the line.
This provides consistent results even with varying voltage levels from other sources connected along the chain. Additionally, this type of TAP accelerates transmissions at any location required in order to improve performance times.
What Are the Benefits of a Network TAP?
Network TAPs have become increasingly popular in recent years as organizations strive to increase their security measures and ensure their networks are always running smoothly. With the ability to monitor multiple ports simultaneously, Network TAPs provide an efficient and cost-effective solution for organizations looking to gain better visibility into what is happening across their networks.
Additionally, with features such as bypass protection, packet aggregation, and filtering capabilities, Network TAPs can also provide organizations with a secure way to maintain their networks and respond quickly to potential threats.
Network TAPs provide organizations with several benefits, such as:
- Increased visibility into network traffic flows.
- Improved security and compliance.
- Reduced downtime by providing greater insight into the cause of any issues.
- Increased network availability by allowing for full duplex monitoring capabilities.
- Reduced cost of ownership since they are typically more economical than other solutions.
Network TAP vs. SPAN Port Mirror(How to Capture Network Traffic? Network Tap vs Port Mirror?):
Network TAPs (Traffic Access Points) and SPAN (Switched Port Analyzer) ports are two essential tools for monitoring network traffic. While both provide visibility into networks, subtle differences between the two must be understood to determine which is best suited for a particular situation.
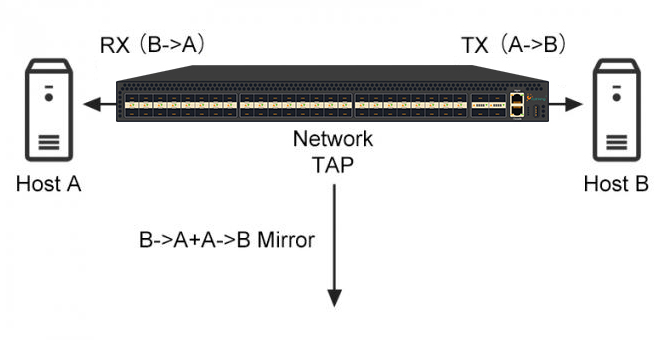
A Network TAP is an external device that connects to the point of connection between two devices that allows the monitoring of the communications passing through it. It does not alter or interfere with the data being transmitted and is not dependent on the switch configured to use it.
On the other hand, a SPAN port is a special type of switch port in which incoming and outgoing traffic is mirrored to another port for monitoring purposes. SPAN ports can be more difficult to configure than Network TAPs, and also require the use of a switch to be used.
Therefore, Network TAPs are more suitable for situations requiring maximum visibility, while SPAN ports are best for simpler monitoring tasks.
Post time: Jul-12-2024