Everyone in life more or less contact with IT and OT pronoun, we must be more familiar with IT, but OT may be more unfamiliar, so today to share with you some of the basic concepts of IT and OT.
What is Operational Technology (OT)?
Operational technology (OT) is the use of hardware and software to monitor and control physical processes, devices, and infrastructure. Operational technology systems are found across a large range of asset-intensive sectors. They are performing a wide variety of tasks ranging from monitoring critical infrastructure (CI) to controlling robots on a manufacturing floor.
OT is used in a variety of industries including manufacturing, oil and gas, electrical generation and distribution, aviation, maritime, rail, and utilities.
IT (Information Technology) and OT (Operational Technology) are two commonly used terms in the industrial field, representing information technology and operational technology respectively, and there are certain differences and connections between them.
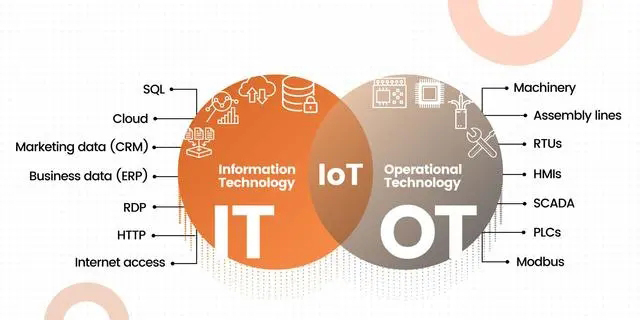
IT (Information Technology) refers to the technology involving computer hardware, software, network and data management, which is mainly used to process and manage enterprise-level information and business processes. IT mainly focuses on the data processing, network communication, software development and operation and maintenance of enterprises, such as internal office automation systems, database management systems, network equipment, etc.
Operational Technology (OT) refers to the technology related to actual physical operations, which is mainly used to handle and control field equipment, industrial production processes, and security systems. OT focuses on aspects of automation control, monitoring sensing, real-time data acquisition and processing on factory production lines, such as production control systems (SCADA), sensors and actuators, and industrial communication protocols.
The connection between IT and OT is that the technology and services of IT can provide support and optimization for OT, such as the use of computer networks and software systems to achieve remote monitoring and management of industrial equipment; At the same time, the real-time data and production status of OT can also provide important information for IT's business decisions and data analysis.
The integration of IT and OT is also an important trend in the current industrial field. By integrating the technology and data of IT and OT, more efficient and intelligent industrial production and operation management can be achieved. This enables factories and enterprises to better respond to market demand changes, improve production efficiency and quality, and reduce costs and risks.
-
What is OT Security?
OT security is defined as the practices and technologies which are used to:
(a) Protect people, assets, and information,
(b) Monitor and/or control physical devices, processes and events, and
(c) Initiate state changes to enterprise OT systems.
OT security solutions include a wide range of security technologies from next-generation firewalls (NGFWs) to security information and event management (SIEM) systems to identity access and management, and much more.
Traditionally, OT cyber security was not necessary because OT systems were not connected to the internet. As such, they were not exposed to outside threats. As digital innovation (DI) initiatives expanded and IT OT networks converged, organizations tended to bolt-on specific point solutions to address specific issues.
These approaches to OT security resulted in a complex network where solutions could not share information and provide full visibility.
Often, IT and OT networks are kept separate which leads to duplicating security efforts and eschewing transparency. These IT OT networks cannot track what is happening throughout the attack surface.
-
Typically, OT networks report to the COO and IT networks report to the CIO, resulting in two network security teams each protecting half of the total network. This can make it difficult to identify the boundaries of the attack surface because these disparate teams do not know what is attached to their own network. In addition to being difficult to efficiently manage, OT IT networks leaves some huge gaps in security.
As explains its approach to OT security, it is to detect threats early using full situational awareness of IT and OT networks.
IT (Information Technology) vs. OT (Operational Technology)
Definition
IT (Information Technology): Refers to the use of computers, networks, and software to manage data and information in business and organizational contexts. It includes everything from hardware (servers, routers) to software (applications, databases) that supports business operations, communication, and data management.
OT (Operational Technology): Involves hardware and software that detects or causes changes through direct monitoring and control of physical devices, processes, and events in an organization. OT is commonly found in industrial sectors, such as manufacturing, energy, and transportation, and includes systems like SCADA (Supervisory Control and Data Acquisition) and PLCs (Programmable Logic Controllers).
Key Differences
| Aspect | IT | OT |
| Purpose | Data management and processing | Control of physical processes |
| Focus | Information systems and data security | Automation and monitoring of equipment |
| Environment | Offices, data centers | Factories, industrial settings |
| Data Types | Digital data, documents | Real-time data from sensors and machinery |
| Security | Cybersecurity and data protection | Safety and reliability of physical systems |
| Protocols | HTTP, FTP, TCP/IP | Modbus, OPC, DNP3 |
Integration
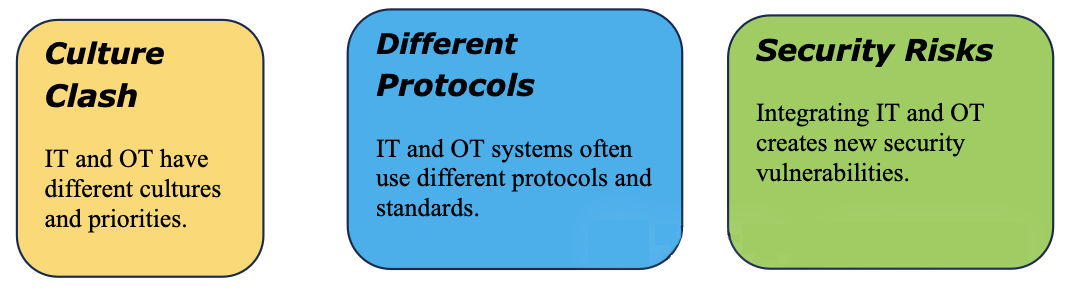
With the rise of Industry 4.0 and the Internet of Things (IoT), the convergence of IT and OT is becoming essential. This integration aims to enhance efficiency, improve data analytics, and enable better decision-making. However, it also introduces challenges related to cybersecurity, as OT systems were traditionally isolated from IT networks.
Related Article: Your Internet of Things Need a Network Packet Broker for Network Security
Post time: Sep-05-2024