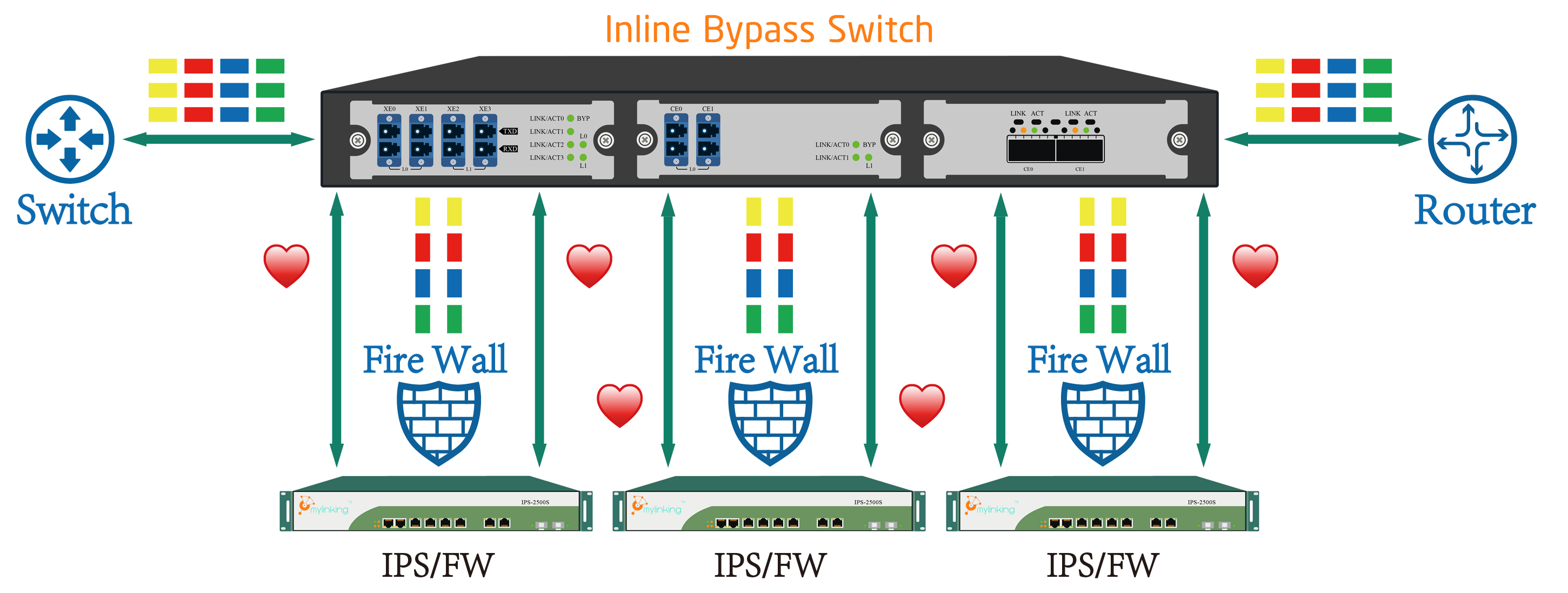
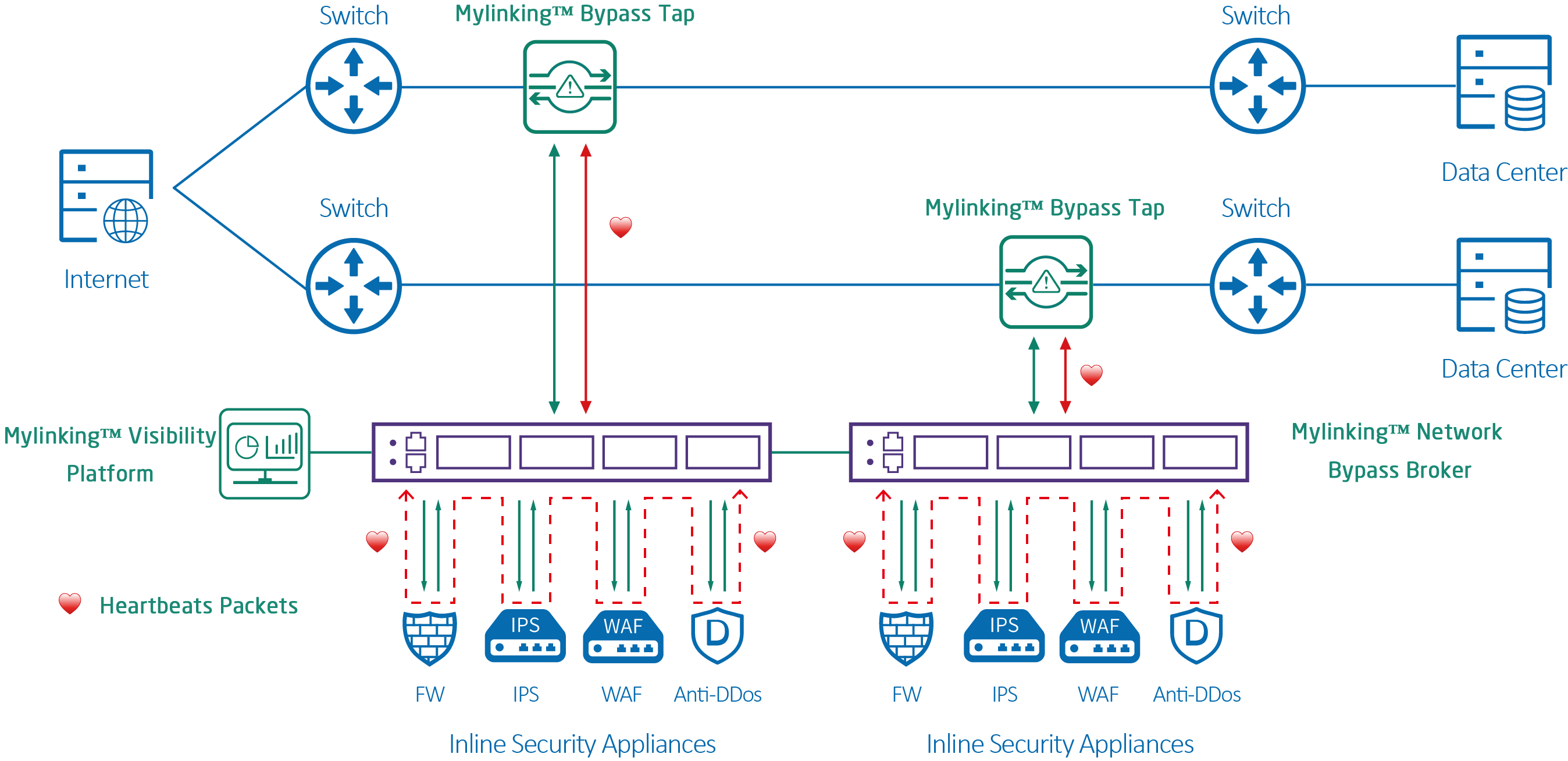
Mylinking™ Network Bypass TAPs with heartbeat technology provide real-time network security without sacrificing network reliability or availability. Mylinking™ Network Bypass TAPs with 10/40/100G Bypass module provide the high-speed performance needed to connect security tools and protect network traffic in real-time without packet loss.
First, what is Bypass?
Generally, a network security device is used between two or more networks, such as an Intranet and an external network. The application program on the network security device analyzes the network packets to determine whether threats exist, and then forwards the packets according to certain routing rules. If the network security device is faulty, For example, after the power failure or crash, the network segments connected to the device will lose contact with each other. At this time, if each network needs to be connected to each other, it must be Bypass forward.
Bypas, as the name implies, is a bypassed function, which means that two networks can be physically routed directly through the network security device's system through a specific trigger state (power failure or shutdown). After the Bypass is enabled, when the network security device fails, the network connected to the bypass device can communicate with each other. In this case, the bypass device does not process packets on the network.
Second, the Bypass classification is applied in the following ways:
Bypass is divided into the following modes: control mode or trigger mode
1. Triggered by the power supply. In this mode, the Bypass function is enabled when the device is not powered on. When the device is powered on, the Bypass is immediately turned off.
2. Controlled by GPIO. After logging in to the OS, you can use GPIO to operate specific ports to control the Bypass switch.
3, by Watchdog control. This is an extension of Method 2. You can use the Watchdog to control the enable and disable of the GPIO Bypass program, so as to control the Bypass status. In this way, the Bypass can be opened by Watchdog if the platform crashes.
In practical applications, these three states often exist at the same time, especially the two ways 1 and 2. The general application method is: When the device is powered off, the Bypass is on. After the device is powered on, the BIOS can operate the Bypass. After the BIOS takes over the device, the Bypass is still on. The Bypass is turned off so that the application can function. During the entire startup process, there is almost no network disconnection.
Last, Analysis of the principle of Bypass implementation
1. Hardware level
On the hardware level, relay is mainly used to realize Bypass. These relays are mainly connected to signal cables of each network port on the Bypass network port. The following figure uses one signal cable to illustrate the working mode of the relay.
Take power trigger as an example. In the case of power failure, the switch in the relay will jump to 1, that is, the Rx in the RJ45 port of LAN1 directly communicates with the RJ45 Tx of LAN2. When the device is powered on, the switch will connect to 2. You need to do that through an app on this device.
2. Software level
In the classification of Bypass, GPIO and Watchdog are discussed to control and trigger the Bypass. In fact, both of these methods operate the GPIO, and then the GPIO controls the relay on the hardware to make the corresponding jump. Specifically, if the corresponding GPIO is set to high, then the relay will jump to position 1. Conversely, if the GPIO cup is set to low, the relay will jump to position 2.
For Watchdog Bypass, in fact, on the basis of the above GPIO control, add Watchdog control Bypass. After the watchdog takes effect, set the action to bypass in the BIOS. The system enables the Watchdog function. After the Watchdog takes effect, the corresponding network port Bypass is enabled, making the device in Bypass state. In fact, the Bypass is also controlled by GPIO. In this case, the low-level writing to GPIO is performed by Watchdog, and no additional programming is required to write GPIO.
The hardware Bypass function is a necessary function of network security products. When the device is powered off or interrupted, the internal and external ports can be physically connected to each other to form a network cable. In this way, users' data traffic can pass through the device without being affected by the current status of the device.
Post time: Feb-06-2023