Ensuring the security of networks in a rapidly changing IT environment and the continuous evolution of users requires a range of sophisticated tools to perform real-time analysis. Your monitoring infrastructure may have network and application performance monitoring (NPM/APM), data loggers, and traditional network analyzers, while your defense systems leverage firewalls, intrusion protection systems (IPS), data leakage prevention (DLP), anti-malware, and other solutions.
No matter how specialized security and monitoring tools are, they all have two things in common:
• Need to know exactly what is happening in the network
• The results of the analysis are based only on the data received
A survey conducted by the Enterprise Management Association (EMA) in 2016 found that nearly 30% of respondents did not trust their tools to receive all the data they needed. This means that there are monitoring blind spots in the network, which ultimately leads to futile efforts, excessive costs, and a higher risk of being hacked.
Visibility requires avoiding wasteful investment and network monitoring blind spots, which requires collecting relevant data on everything going on in the network. The splitters/splitters and mirror ports of network devices, also known as SPAN ports, become the access points used to capture traffic for analysis.
This is a relatively "simple operation"; the real challenge is to efficiently get the data from the network to every tool that needs it. If you only have a few network segments and relatively few analysis tools, the two can be directly connected. However, given the speed at which networks continue to scale, even if it is logically possible, there is a good chance that this one-to-one connection will create an intractable management nightmare.
EMA reported that 35% of enterprise institutions cited the shortage of SPAN ports and splitters as the main reason why they were unable to fully monitor their network segments. Ports on high-end analysis tools such as firewalls may also be scarcer, so it's critical that you don't overload your equipment and degrade performance.
Why do you need Network Packet Brokers?
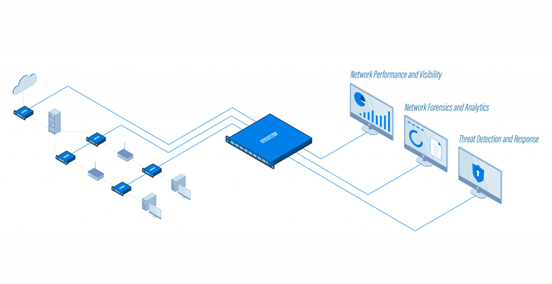
The Network Packet Broker (NPB) is installed between the splitter or SPAN ports used to access network data, as well as security and monitoring tools. As the name suggests, the basic function of the network packet broker is: to coordinate the network packet data to ensure that each analysis tool accurately obtains the data it needs.
NPB adds an increasingly critical layer of intelligence that reduces cost and complexity, helping you to:
To obtain more comprehensive and accurate data for better decision-making
Network packet broker with advanced filtering capabilities is used to provide accurate and effective data for your monitoring and security analysis tools.
Tighter security
When you can't detect a threat, it's hard to stop it. NPB is designed to ensure that firewalls, IPS, and other defense systems always have access to the exact data they need.
Solve problems faster
In fact, just identifying the problem accounts for 85% of the MTTR. Downtime means money lost, and mishandling it can have a devastating impact on your business.
Context-aware filtering provided by NPB helps you discover and determine the root cause of problems faster by introducing advanced application intelligence.
Increase initiative
The metadata provided by smart NPB through NetFlow also facilitates access to empirical data to manage bandwidth usage, trends, and growth to nip the problem in the bud.
Better return on investment
Smart NPB can not only aggregate traffic from monitoring points like switches, but also filter and collate data to improve the utilization and productivity of security and monitoring tools. By handling only the relevant traffic, we can improve tool performance, reduce congestion, minimize false positives, and achieve greater security coverage with fewer devices.
Five ways to improve ROI with Network Packet Brokers:
• Faster troubleshooting
• Detect vulnerabilities faster
• Reduce the burden of security tools
• Extend the life of monitoring tools during upgrades
• Simplify compliance
What exactly can the NPB do?
Aggregating, filtering, and delivering data sounds simple in theory. But in reality, smart NPB can perform very complex functions, resulting in exponentially higher efficiency and security gains.
Load balancing traffic is one of the functions. For example, if you are upgrading your data center network from 1Gbps to 10Gbps, 40Gbps, or higher, the NPB can slow down to allocate the high-speed traffic to an existing batch of 1G or 2G low-speed analytics monitoring tools. This not only extends the value of your current monitoring investment, but also avoids costly upgrades when IT is migrated.
Other powerful features performed by NPB include:
Redundant data packets are deduplicated
Analysis and security tools support the reception of a large number of duplicate packets forwarded from multiple splitters. NPB can eliminate duplication to prevent tools from wasting processing power when processing redundant data.
SSL Decryption
Secure Socket Layer (SSL) encryption is the standard technique used to securely send private information. However, hackers can also hide malicious cyber threats in encrypted packets.
Examining this data must be decrypted, but decomposing the code requires precious processing power. Leading network packet brokers can offload decryption from security tools to ensure overall visibility while reducing the burden on high-cost resources.
Data Masking
SSL decryption makes the data visible to anyone with access to security and monitoring tools. The NPB can block credit card or Social Security numbers, protected health information (PHI), or other sensitive personally identifiable information (PII) before passing the information, so it is not disclosed to the tool and its administrators.
Header Stripping
NPB can remove headers such as VLAN, VXLAN, L3VPN, so tools that cannot handle these protocols can still receive and process packet data. Context-aware visibility helps to discover malicious applications running on the network and the footprints left by attackers as they work in the system and network.
Application and threat intelligence
Early detection of vulnerabilities reduces sensitive information loss and ultimately vulnerability costs. The context-aware visibility provided by NPB can be used to uncover indicators of intrusion (IOC), identify the geolocation of attack vectors, and combat cryptographic threats.
Application intelligence extends beyond layers 2 to 4 (OSI model) of packet data up to layer 7 (application layer). Rich data on user and application behavior and location can be created and exported to prevent application layer attacks where malicious code masquerads as normal data and valid client requests.
Context-aware visibility helps discover the malicious applications running on your network and the footprints left by attackers as they work through your system and network.
Application Monitoring
The visibility of application perception also has a profound impact on performance and management. Perhaps you want to know when employees used cloud-based services such as Dropbox or web-based email to bypass security policies and transfer company files, or when former employees tried to access files using cloud-based personal storage services.
The benefits of NPB
• Easy to use and manage
• Intelligence to remove team burdens
• No packet loss - runs advanced features
• 100% reliability
• High performance architecture
Post time: Jan-20-2025