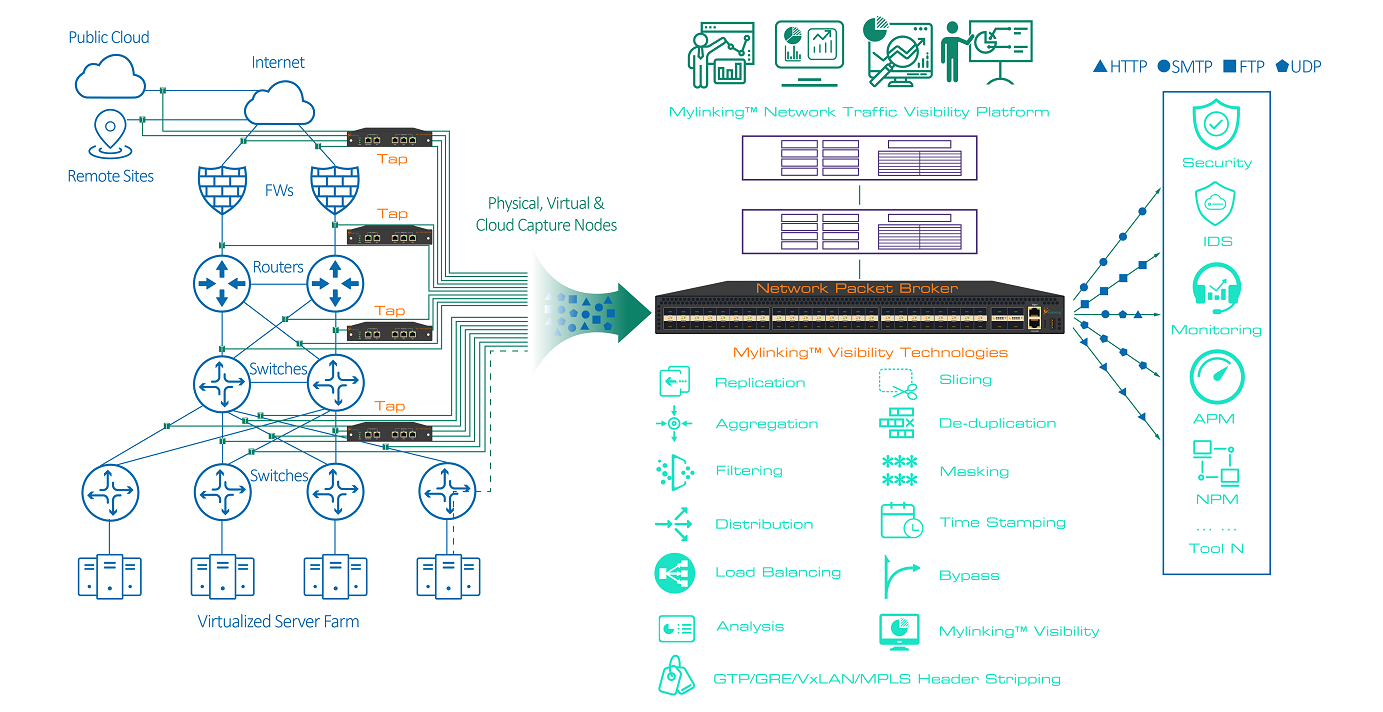
Introduction
Network Traffic is the total number of packets passing through the network link in unit time, which is the basic index to measure network load and forwarding performance. Network traffic monitoring is to capture the overall data of network transmission packets and statistics, and network traffic data capturing is the capturing of network IP data packets.
With the expansion of the data center Q network scale, the application system is more and more abundant, the network structure is more and more complex, the network services on the network resources requirements are higher and higher, the network security threats are more and more, the operation and maintenance of refined requirements continue to improve, network traffic collection and analysis has become an indispensable analysis means of data center infrastructure. Through the in-depth analysis of network traffic, network managers can speed up fault location, analyze application data, optimize network structure, system performance and security control more intuitively, and speed up fault location. Network traffic collection is the basis of traffic analysis system. A comprehensive, reasonable and effective traffic capturing network is helpful to improve the efficiency of network traffic capturing, filtering and analysis, meet the needs of traffic analysis from different angles, optimize network and business performance indicators, and improve user experience and satisfaction.
It is very important to study the methods and tools of network traffic capturing for effectively understanding and using the network, accurately monitoring and analyzing the network.
The Value of Network Traffic Collection/Capturing
For data center operation and maintenance, through the establishment of a unified network traffic capturing platform, combined with the monitoring and analysis platform can greatly improve the operation and maintenance management and business continuity management level.
1. Provide Monitoring and Analysis Data Source: The traffic of business interaction on the network infrastructure obtained by network traffic capturing can provide the required data source for network monitoring, security monitoring, big data, customer behavior analysis, access strategy requirements analysis and optimization, all kinds of visual analysis platforms, as well as cost analysis, application expansion and migration.
2. Complete Fault Proof Traceability Ability: through network traffic capturing, it can realize back analysis and fault diagnosis of historical data, provide historical data support for development, application and business departments, and completely solve the problem of difficult evidence capturing, low efficiency and even deniability.
3. Improve the Efficiency of Fault Handling. By providing a unified data source for network, application monitoring, security monitoring and other platforms, it can eliminate the inconsistency and asymmetry of information collected by the original monitoring platforms, improve the efficiency of handling all kinds of emergencies, quickly locate the problem, resume business, and improve the level of business continuity.
Classification of Network Traffic Collection/Capturing
Network traffic capturing is mainly to monitor and analyze the characteristics and changes of computer network data flow in order to grasp the traffic characteristics of the whole network. According to the different sources of network traffic, the network traffic is divided into network node port traffic, end-to-end IP traffic, service traffic of specific services and complete user service data traffic.
1. Network Node Port Traffic
Network node port traffic refers to the information statistics of incoming and outgoing packets at the network node device port. It includes the number of data packets, number of bytes, packet size distribution, packet loss and other non-learning statistical information.
2. End-to-end IP Traffic
End-to-end IP traffic refers to the network layer from a source to a destination! Statistics of P packets. Compared with the network node port traffic, the end-to-end IP traffic contains more abundant information. Through the analysis of it, we can know the destination network that the users in the network access, which is an important basis for network analysis, planning, design and optimization.
3. Service Layer Traffic
The service layer traffic contains information about the ports of the fourth layer (TCP day layer) in addition to the end-to-end IP traffic. Obviously, it contains information about the kinds of application services that can be used for more detailed analysis.
4. Complete User Business Data Traffic
The complete user service data traffic is very effective for the analysis of security, performance and other aspects. Capturing the complete user service data requires super strong capture ability and super high hard disk storage speed and capacity. For example, capturing the incoming data packets of hackers can stop certain crimes or obtain important evidence.
Common Method of Network Traffic Collection/Capturing
According to the characteristics and processing methods of network traffic capturing, traffic capturing can be divided into the following categories: partial collection and complete collection, active collection and passive collection, centralized collection and distributed collection, hardware collection and software collection, etc. With the development of traffic collection, some efficient and practical traffic collection methods have been produced based on the above classification ideas.
The network traffic collection technology mainly includes the monitoring technology based on traffic mirror, the monitoring technology based on real-time packet capture, the monitoring technology based on SNMP/RMON, and the monitoring technology based on network traffic analysis protocol such as NetiowsFlow. Among them, the monitoring technology based on traffic mirror includes the virtual TAP method and the distributed method based on hardware probe.
1. Based on Traffic Mirror Monitoring
The principle of network traffic monitoring technology based on full mirror is to achieve lossless copy and image collection of network traffic through the port mirror of network equipment such as switches or additional equipment such as optical splitter and network probe. The monitoring of the whole network needs to adopt a distributed scheme, deploying a probe in each link, and then collecting the data of all probes through the background server and database, and doing traffic analysis and long-term report of the whole network. Compared with other traffic collection methods, the most important feature of traffic image collection is that it can provide rich application layer information.
2. Based on Real-time Packet Capture Monitoring
Based on real-time packet capture analysis technology, it mainly provides detailed data analysis from the physical layer to the application layer, focusing on protocol analysis. It captures the interface packets in a short time for analysis, and is often used to realize the rapid diagnosis and solution of network performance and fault. It has the following shortcomings: it cannot capture packets with large traffic and long time, and it cannot analyze the traffic trend of users.
3. Monitoring Technology based on SNMP/RMON
Traffic monitoring based on SNMP/RMON protocol collects some variables related to specific equipment and traffic information through network device MIB. It includes: number of input bytes, number of input non-broadcast packets, number of input broadcast packets, number of input packet drops, number of input packet errors, number of input unknown protocol packets, number of output packets, number of output non-broadcast packets, number of output broadcast packets, number of output packet drops, number of output packet errors, etc. Since most routers now support standard SNMP, the advantage of this method is that no additional data acquisition equipment is needed. However, it only includes the most basic content such as the number of bytes and the number of packets, which is not suitable for complex traffic monitoring.
4. Netflow-based Traffic Monitoring Technology
Based on the traffic monitoring of Nethow, the traffic information provided is expanded to the number of bytes and packets based on the five-tuple (source IP address, destination IP address, source port, destination port, protocol number) statistics, which can distinguish the flow on each logical channel. The monitoring method has high efficiency of information collection, but it can not analyze the information of physical layer and data link layer, and needs to consume some routing resources. It usually needs to attach a separate function module to the network equipment.
Post time: Oct-17-2024