Technical Blog
-
A Network Packet Broker with 64*100G/40G QSFP28 upto 6.4Tbps Traffic Process Capability
Mylinking™ has developed a new product, the Network Packet Broker of ML-NPB-6410+, which is designed to provide advanced traffic control and management capabilities for modern networks. In this technical blog, we will take a closer look at the features, abilities, applic...Read more -
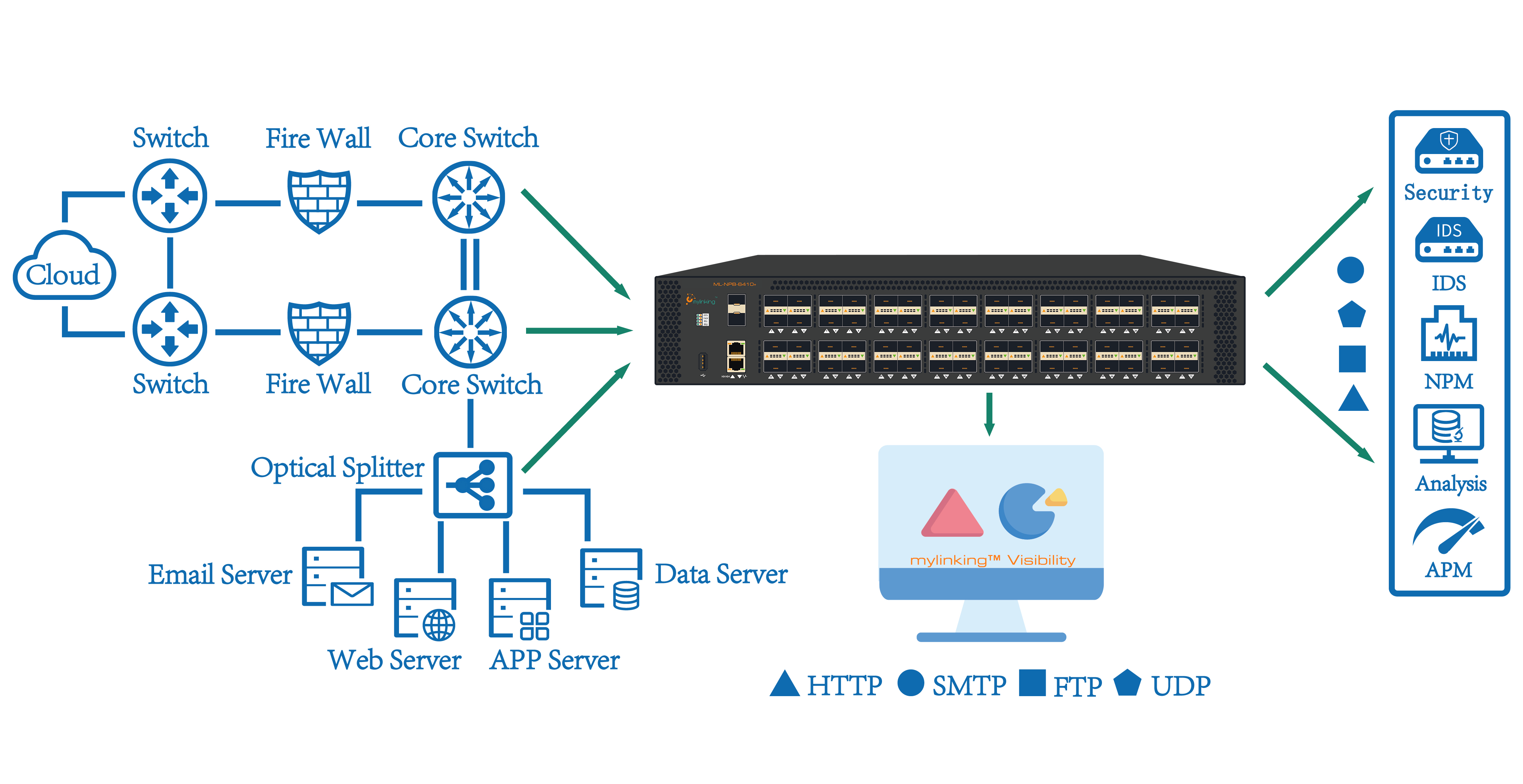
To simplify & optimize your network infrastructure with Mylinking™ Network Packet Broker
In today's world, network traffic is increasing at an unprecedented rate, which makes it challenging for network administrators to manage and control the flow of data across various segments. To address this issue, Mylinking™ has developed a new product, the Network Pack...Read more -
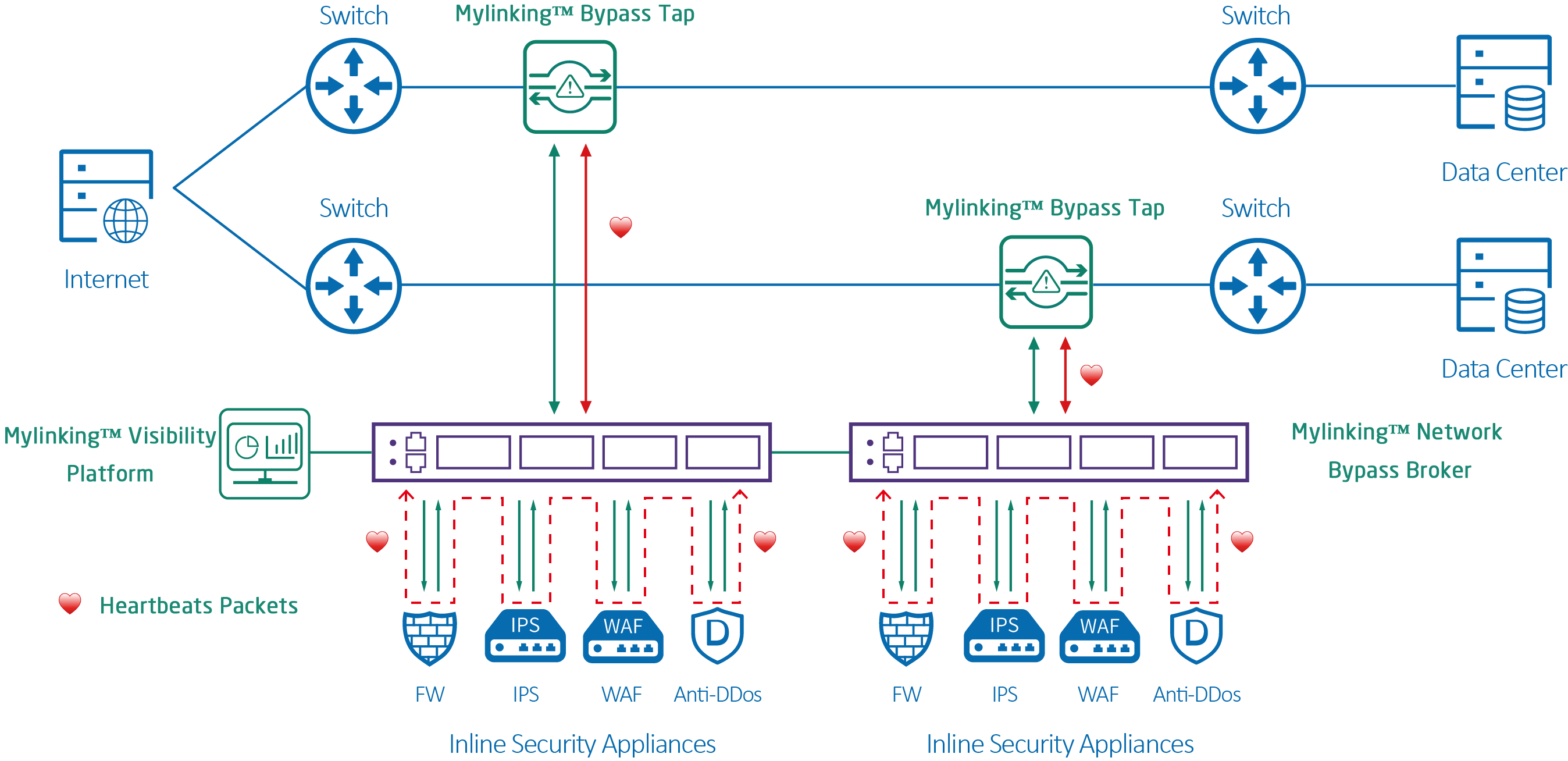
How to Deploy Inline Bypass Tap to Prevent Overload or Crash of Safety Tools?
The Bypass TAP (also called the bypass switch) provides fail-safe access ports for embedded active security devices such as IPS and next-generation firewalls (NGFWS). The bypass switch is deployed between network devices and in front of network security tools to provide ...Read more -
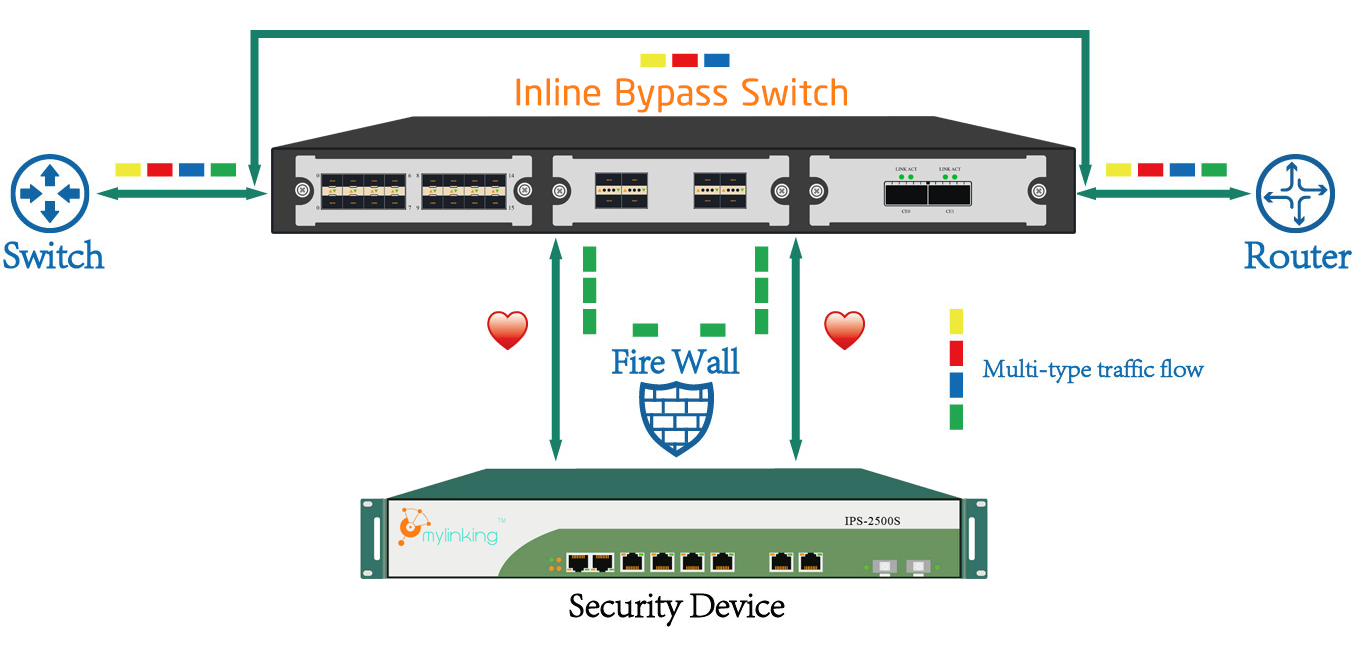
What the Mylinking™ Active Network Bypass TAPs can do for you?
Mylinking™ Network Bypass TAPs with heartbeat technology provide real-time network security without sacrificing network reliability or availability. Mylinking™ Network Bypass TAPs with 10/40/100G Bypass module provide the high-speed performance needed to connect security...Read more -
Network Packet Broker to Capture Switch Traffic on SPAN, RSPAN and ERSPAN
SPAN You can use the SPAN function to copy packets from a specified port to another port on the switch that is connected to a network monitoring device for network monitoring and troubleshooting. SPAN does not affect the packet exchange between the source port and the de...Read more -

Your Internet of Things Need a Network Packet Broker for Network Security
There’s no doubt that 5G Network is important, promising the high speeds and unparalleled connectivity that are required to unleash the full potential of the “Internet of Things” also as "IoT" — the ever-growing network of web-connected devices—and artificial intelligenc...Read more -
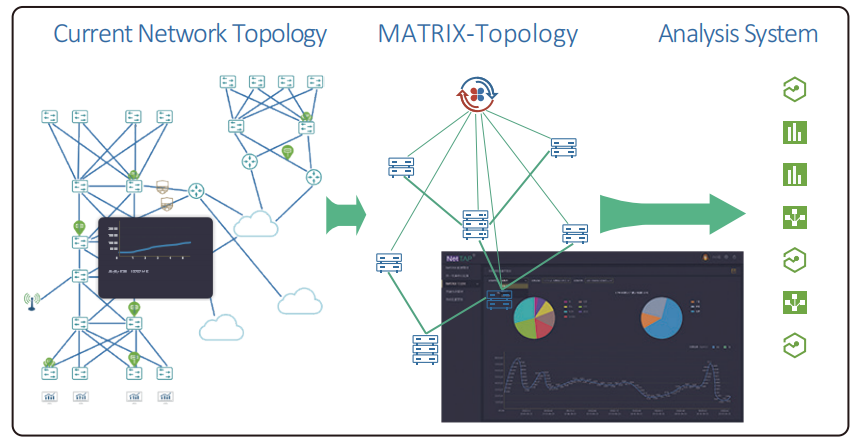
The Network Packet Broker Application in Matrix-SDN(Software Defined Network)
What is SDN? SDN: Software Defined Network, which is a revolutionary change that solves some of the inevitable problems in traditional networks, including lack of flexibility, slow response to demand changes, inability to virtualize the network, and high costs.Under the ...Read more -
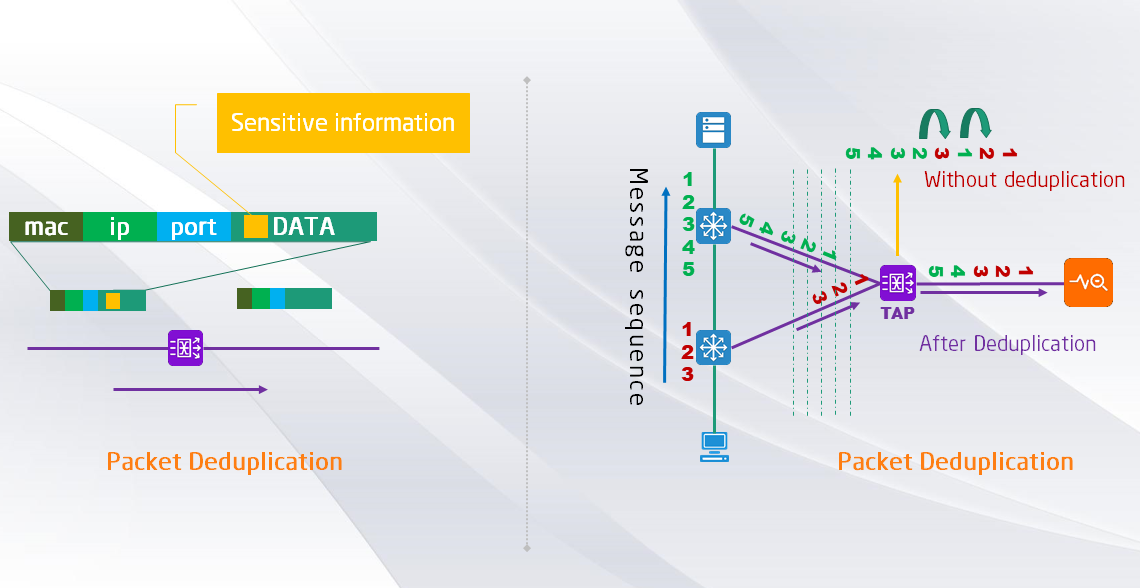
Network Packet De-duplication for your Data Optimization via Nework Packet Broker
Data De-duplication is a popular and popular storage technology that optimizes storage capacity.It eliminates redundant data by removing duplicate data from the dataset, leaving only one copy.As shown in the figure below.This technology can greatly reduce the need for ph...Read more -
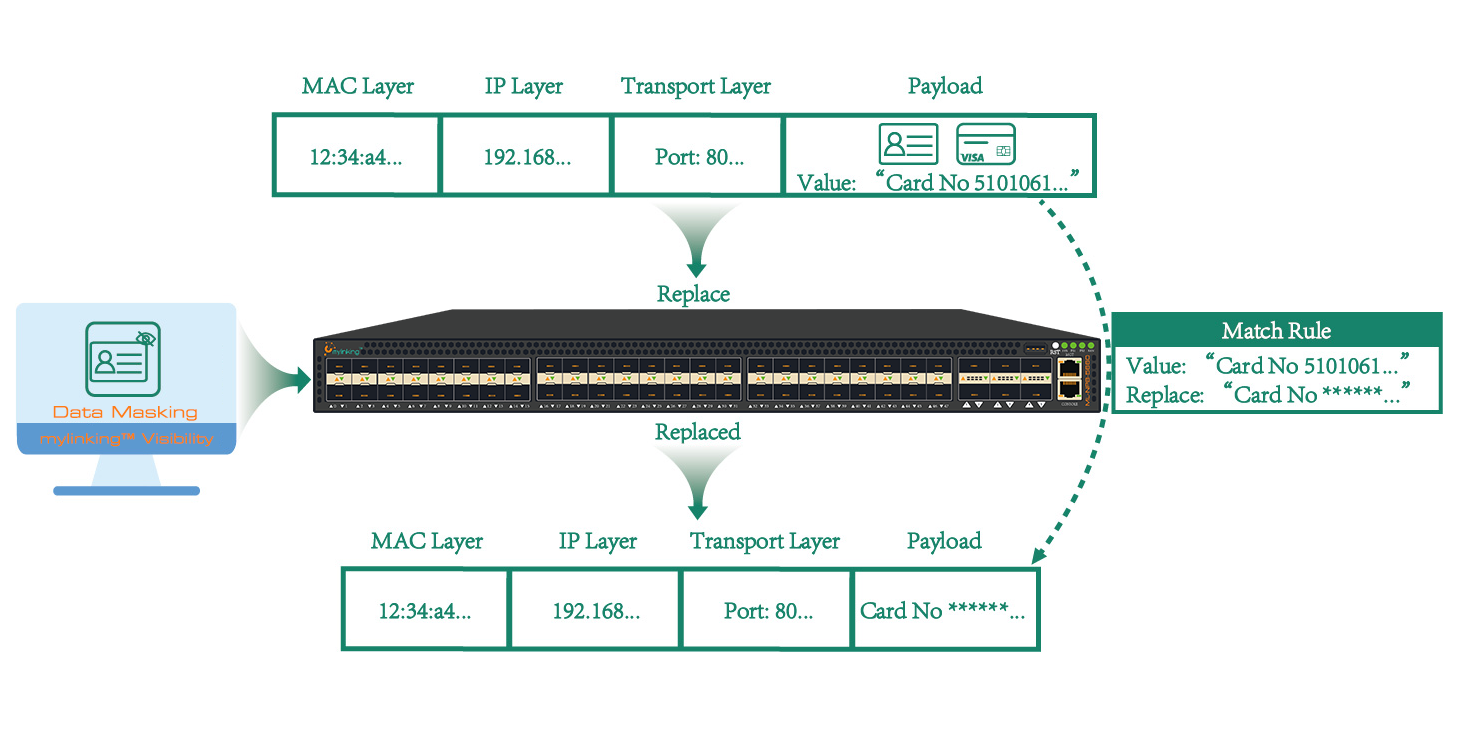
What’s the Data Masking Technology and Solution in Network Packet Broker?
1. The concept of Data Masking Data masking is also known as data masking. It is a technical method to convert, modify or cover sensitive data such as mobile phone number, bank card number and other information when we have given masking rules and policies. This techniqu...Read more -
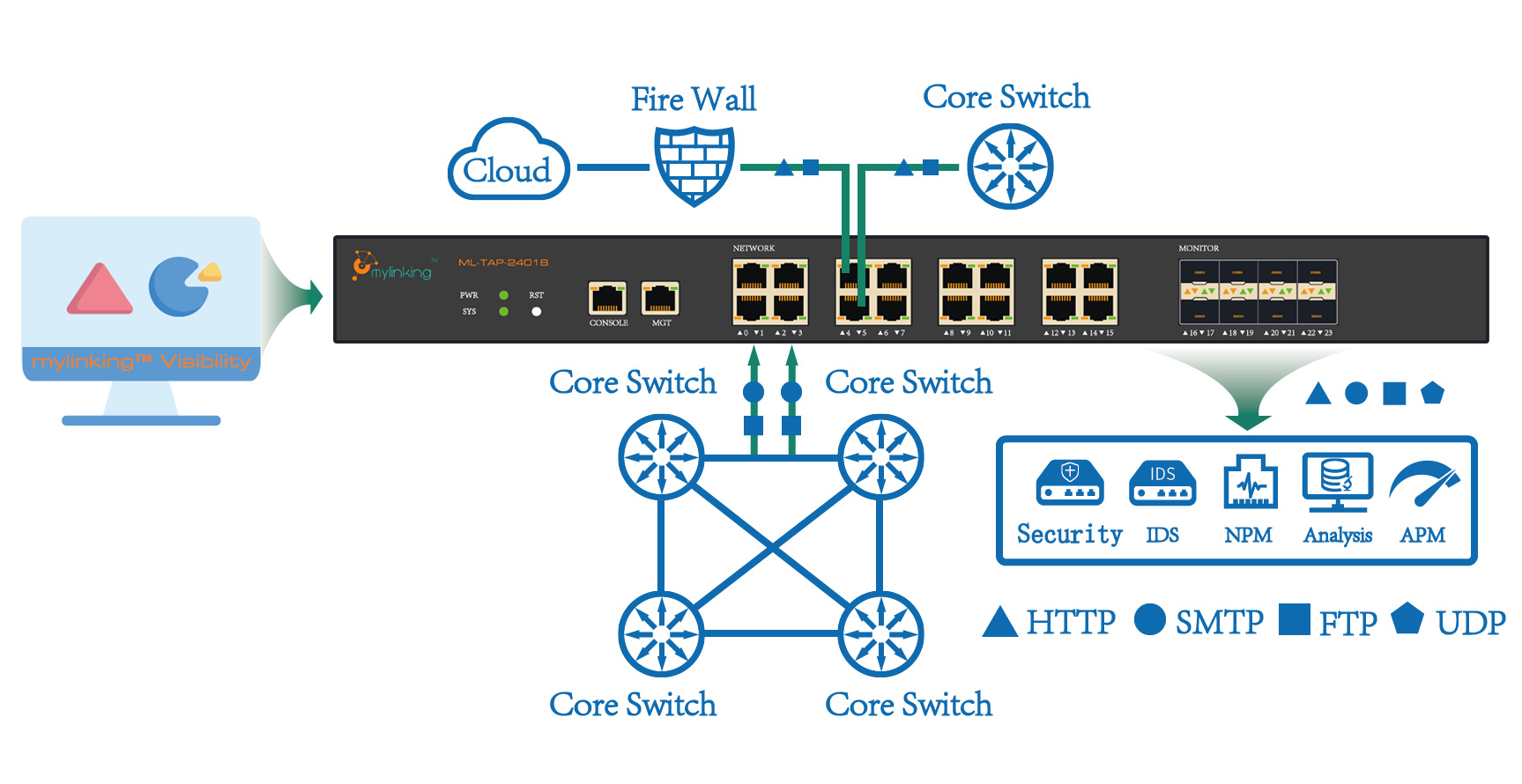
What’s features of the Network Packet Broker(NPB) & Test Access Port (TAP)?
The Network Packet Broker (NPB), which includes the commonly used 1G NPB, 10G NPB, 25G NPB, 40G NPB, 100G NPB, 400G NPB, and Network Test Access Port (TAP), is a hardware device that plugs directly into the network cable and sends a piece of network communication to othe...Read more -
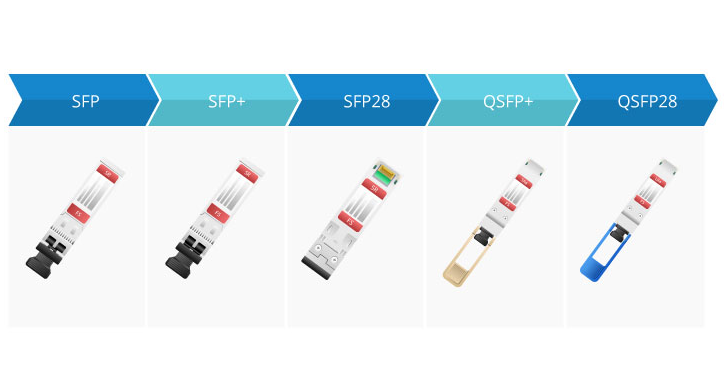
What’s the differences between SFP, SFP+, SFP28, QSFP+ and QSFP28?
SFP SFP can be understood as an upgraded version of GBIC. Its volume is only 1/2 of that of GBIC module, which greatly increases the port density of network devices. In addition, the SFP's data transfer rates range from 100Mbps to 4Gbps. SFP+ SFP+ is an enhanced version...Read more -

The differences between Network TAP and Network Switch Port Mirror
To monitor network traffic, such as user online behavior analysis, abnormal traffic monitoring, and network application monitoring, you need to collect network traffic. Capturing network traffic may be inaccurate. In fact, you need to copy the current network traffic and...Read more

















